Protect your customers' identity and transactions with our user authentication solution.
User Authentication System

Discover our authentication and access control solution
Authentication is “the electronic process that makes possible the electronic identification of a natural or legal person, or the origin and integrity of data in electronic format”. This is defined in Article 3.5 of the eIDAS Regulation.
After verifying your customer’s identity, it is necessary to enable secure access to platforms and systems for them to interact with them, while protecting their information, transactions and privacy. Authentication with guarantees further reinforces the security of your company and that of the legitimate customer. It thus plays a key role in preventing fraud.
Our user authentication tool uses several of these factors, combined according to the characteristics of each process:
- Inherence (what is): something that is the user. It is a biometric factor impossible to forge like the face (facial recognition) or fingerprints.
- Knowledge (what is known): something known only to the user, such as a PIN or password.
- Possession (what one has): something that only the user possesses. For example, the phone to receive an OTP (One Time Password) or a security token.
THE USER AUTHENTICATION PROCESS, STEP BY STEP
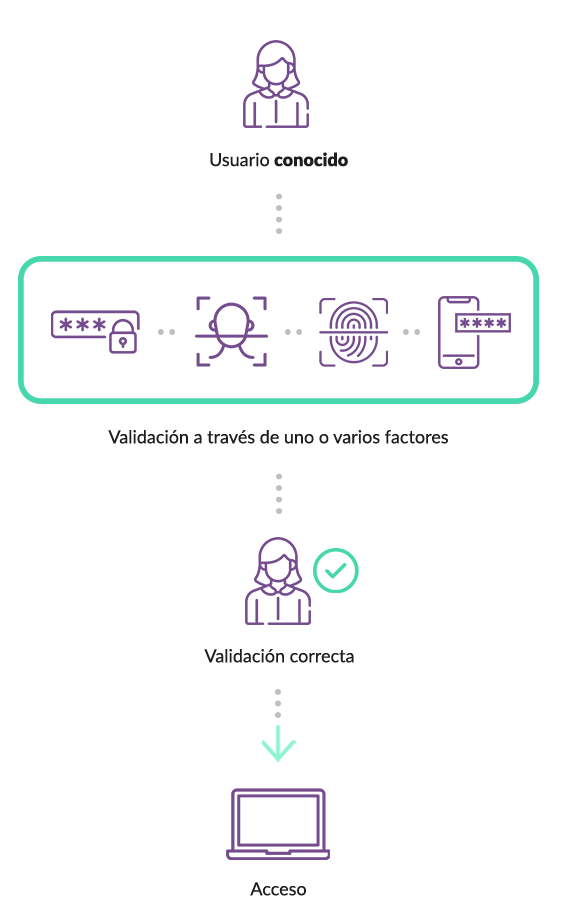
Select one or more of the factors you want to use during the authentication process for secure access control to platforms, systems and private areas:
- Password.
- Security questions with pre-defined answers.
- One-time password (OTP). The customer enters the code received by SMS or PUSH app notification to the cell phone or email.
- Biometrics: the most secure form of authentication. Biometric data are very difficult to falsify.
- Qualified electronic certificate.
In cases of multiple factor selection, the practitioner will have to prioritize which factor to apply first. Our tool and our technical team then builds the customized process.
Benefits of authentication in the user access control process
 Possibility of including one or more user authentication factors.
Possibility of including one or more user authentication factors.
 Maximum protection for access to high security areas such as banks or institutions with sensitive documents or data.
Maximum protection for access to high security areas such as banks or institutions with sensitive documents or data.
 We put the customer at the center. Providing you with a smooth, engaging and reliable user experience.
We put the customer at the center. Providing you with a smooth, engaging and reliable user experience.
 It offers great security over the management process that minimizes frictions and fraud risks.
It offers great security over the management process that minimizes frictions and fraud risks.
 Enables the optimization of security and reduction of costs related to fraudulent operations.
Enables the optimization of security and reduction of costs related to fraudulent operations.
Our tool for the authentication of your customers is of interest to you for…
- Protect your customers’ information and the integrity of your systems.
- Minimize the risk of fraud.
- To offer a reliable service in sectors where security is key for the customer.
- Avoid reputational problems thanks to a robust and reliable system.
How does our authentication solution for people access control work?
We can structure uni or multifactor authentication processes, depending on the criticality of the process for which access is given. From our experience and knowledge we designed a user authentication flow that balances agility in the customer experience with security. The objective is to provide the service or system while minimizing frictions and risks.
![]() Something the customer knows:
Something the customer knows:
- Password
- Security question
 Something the customer owns:
Something the customer owns:
- OTP via SMS or email
- Coordinates card
- Electronic certificate
- Identity card
 Something we are:
Something we are:
- Facial biometrics
- Voice biometrics
- Fingerprints
Does your company need user authentication solutions?
OTHER SOLUTIONS ON CERTIFIED DIGITAL IDENTIFICATION
Frequently Asked Questions
The main mission of our user authentication system is to verify, in a reliable way, that the person who wants to access a platform, a system or a private area is who he/she claims to be and who has the enabled access. This prevents outsiders from coming into contact with private and, in many cases, sensitive information.
There are several methods of secure user authentication that can be used individually or in multifactor mode, combining several of them. These methods can be based on three categories:
- Something the customer knows: password or security questions.
- Something that the customer possesses: OTP, coordinate card, electronic certificate, official identity document…
- Something the customer is: facial and voice biometrics or fingerprints.
The first thing is to choose a quality technology provider, ideally one that is recognized as a qualified and trusted provider of electronic services. Then, share with him the specifications, expected use and criticality level of the process to be implemented, as well as the particular needs of the project and secondary needs (e.g., launching legal communications to customers related to the secure user authentication system). When the submitted project offers all the desired solutions, the development and implementation phase begins.
As a general rule, secure authentication systems must comply with cross-cutting regulations such as the RGPD or eIDAS (which defines the process in Article 3.5) or sector-specific regulations, such as PSD and PSD2, which are more focused on financial services.
Among others, to execute an adequate and updated cybersecurity strategy, to execute robust onboarding processes, to maintain fluid communication with users on security and cyber-risk issues and to count on the collaboration of a qualified and trustworthy electronic services provider, which always offers a plus of security, privacy and legal value in the projects it develops.


