Gartner report calls mobile banking the “killer app.
killer app
” (i.e., soon to be indispensable in mobile banking use cases) for biometric authentication.
Are consumers ready for biometrics in retail and banking?
A recent Visa survey of 1,000 US consumers, for example, says yes. The majority of respondents preferred biometric authentication to password-based authentication:
- Respondents said biometrics are easier (70%) and faster (61%) than passwords.
- 52% said they would switch banks if they did not offer biometric authentication in the future.
- The most commonly cited benefits of biometric authentication among respondents were:
- No need to remember multiple passwords / PINs (50%)
- Better security than passwords / PINs (46%)
- Not forgetting/missing an authentication method (33%)
When measuring the quality of the customer experience, transaction abandonment rates are an important metric. Almost 50 per cent of Visa respondents confirmed that they had abandoned an online purchase because they could not remember their password.
“The benefits in CX (
Customer Experience
) benefits of biometric authentication have driven an increase in mobile banking applications in recent years,” states the Gartner report.
Is biometric authentication more reliable than other authentication methods?
It can be argued that yes, biometric authentication is indeed more secure than other authentication methods. The key to a reliable biometric authentication system is the ability to detect or prevent impersonation of the biometric feature of a living person. A fingerprint, “facial print” or whatever biometric modality you choose is not simply another form of password or token.
token
.
Without additional analysis, there is really no way to know who is providing a password. It is only known that the password was entered and that it matches the password registered in the database. On the other hand, a reliable biometric authentication system with effective liveness detection and spoofing mitigations provides an additional indicator of trust, as it validates the subject/person who is offering the biometric sample for verification. Because the fingerprint, face or [insert your favorite biometric modality here] is presented live and relates to the user in person.
Dispelling a misconception about biometric authentication
According to Gartner, “biometric authentication cannot and does not rely on the secrecy of biometric traits, but relies on the difficulty of impersonating the live person presenting the trait on a capture device (sensor). This last point is not widely known, leading to some common misconceptions, reinforced by the detection of the rare presentation attacks (PAD or presentation attack detection) detected on consumer devices and advertising about attacks perpetrated against Apple Touch ID, Samsung swipe sensors, Android facial recognition, etc.”
You’ve probably heard the criticism that “you can’t change your fingerprint or face if these are ever compromised.” That’s right: you can’t change your biometric traits as if they were a password. However, the idea that if a cybercriminal steals your biometric data, he will successfully pass the corresponding authentication challenge at the biometric capture point is wrong.
- You can’t literally steal someone’s face/fingerprint/etc.
1
– Horror movies aside, in reality cybercriminals are generally not looking to remove (i.e., “steal”) someone’s face or fingerprint from their body.
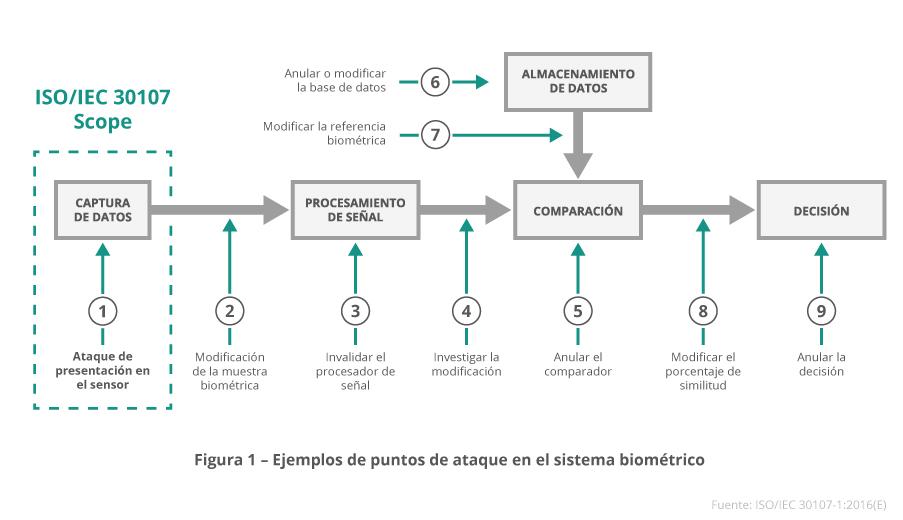
- Live presentation of the biometric feature is the linchpin – As the Gartner report argues, “in a robust fingerprinting method, it should not matter that an attacker can present an exact copy of a person’s fingerprint; anything other than the person’s actual finger (still attached to their living body) should not work.” A presentation attack consists of an enemy presenting a reproduction of a biometric feature (an “impersonation”) that resembles a stored reference for a legitimate user (e.g. 3D printed models, masks, images, video, etc.). Life detection identifies whether the biometric feature presented is of a living human or is a digital or fabricated representation (or again, an impersonation). Presentation Attack Detection (PAD) is a combination of counterfeit detection and liveness detection mechanisms. In some cases, the consumer’s native PAD system may need to be supplemented by biometric systems from a third party. The ISO/IEC 30107 standard establishes a methodology by which the PAD effectiveness of a biometric solution can be measured.
Of course, end-to-end end-to-end of a biometric authentication system does not stop at presentation attacks on the sensor where the biometric data is captured. Replay attacks are an example of another risk, but in many cases, technology that ensures application integrity, such as in-application protection and application shielding /RASP, helps mitigate these risks. But, financial institutions must be careful in the design, implementation, distribution and configuration of the biometric authentication solution.
Interested in this content? Discover our article on How banks can automate their legal communications using the online postal burofax.
