There are many benefits to offer customers, suppliers and partners through the ability to use electronic signatures, but security must remain the focus. Organizations initiating e-signature transactions must know who they are doing business with through online and mobile channels.
According to Forrester Research, “authentication issues are moving to the forefront of attention. Growing adoption and the increased value of transactions conducted electronically have led to an increased focus on fraud, legal challenges and authentication validity.” In an electronic signature transaction, the authentication step contributes to the enforceability of the signed document and validates that a company is transacting with the correct person in the signing process.
As an organization, you must strike the right balance between customer experience and security when implementing user authentication. This will ensure high transaction completion rates and minimize customer frustration and abandonment due to cumbersome authentication processes. Depending on the use case and your authentication needs, the best approach is to look for e-signature software that supports a wide range of authentication methods to ensure the best user experience and mitigate the risk of fraud. In addition, you must ensure that the authentication options can be configured to meet the requirements of your e-signature process and channel. For example, an electronic signature process that occurs face-to-face at a bank branch or with an insurance agent will often use different authentication methods than a remote transaction.
The difference between identification and authentication
The terms “user identification” and “user authentication” may sound similar, but in reality they have different meanings.
User identification is the process of presenting and claiming an identity. This is the first step in determining who you are doing business with, so naturally it is done the first time two parties enter into a transaction. A good example is a new applicant going to the bank to open an account for the first time. The applicant will be asked to prove his identity using his driver’s license, passport or ID card. To verify the identity of a new applicant remotely through your digital channels requires the following
digital identity verification
. A digital identity verification service allows you to quickly and securely confirm that an “unknown user” is who they say they are, directly through their mobile device.
Once the individual’s identity is confirmed, he or she becomes a customer or “known user” and usually receives credentials for future transactions. User authentication is the process of verifying those credentials before giving access to a system, in this case, the electronic signature process.
Electronic signature authentication methods
Unlike a handwritten signature, OneSpan Sign, the e-signature provider MailTecK & Customer Comms works with, offers several authentication methods to ensure that only the correct signers access your e-signature transactions. These authentication methods can be used alone or in combination to verify a person’s identity and create a trusted transaction.
The electronic signature workflow
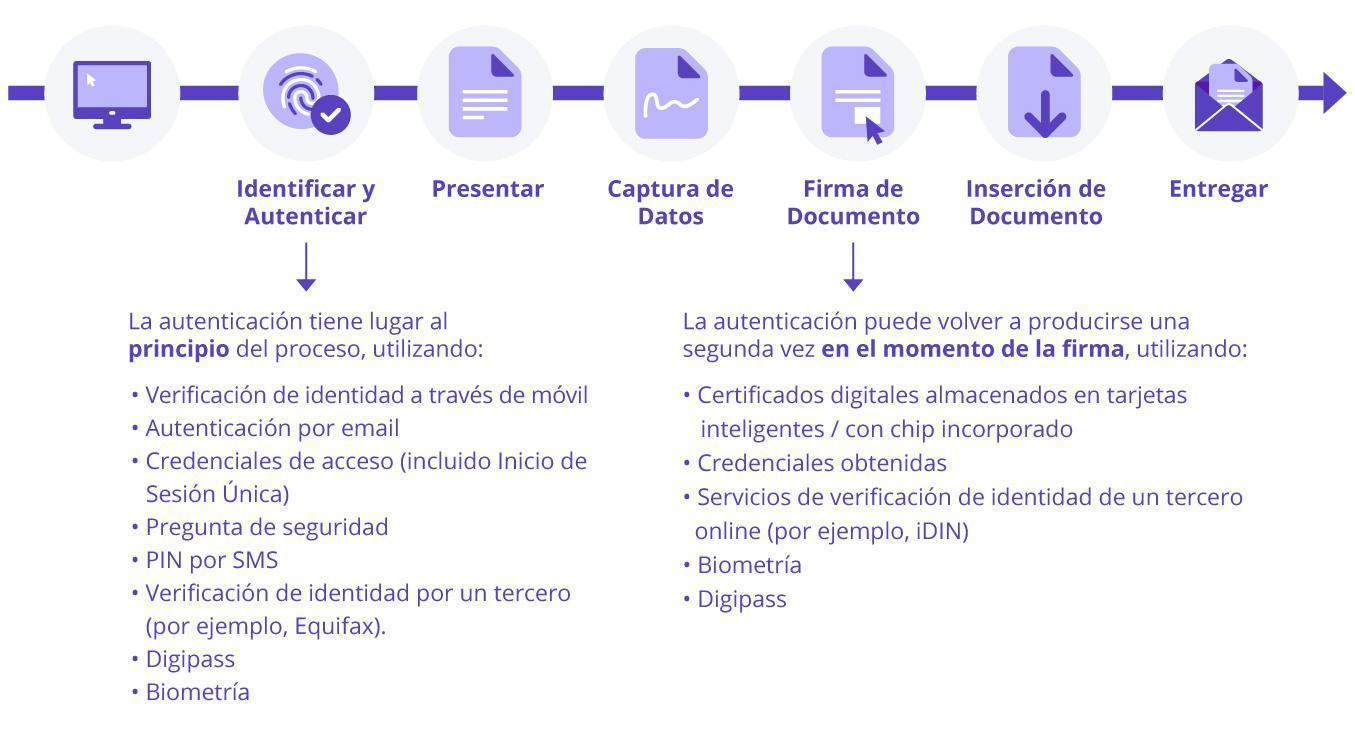
- E-mail authentication: the signatory is sent an e-mail with an embedded link inviting him/her to access the signing process. After clicking on the link, the signer is authenticated. Email authentication establishes a connection to the signer due to the fact that their email address is unique.
- Access credentials (including Single Sign-On):Signatories can be granted access to documents after logging into an online portal or government services portal with a valid username and password. Using the example of the online banking portal, the customer logs into their account and is presented with the documents to be electronically signed within the portal.
- OTP via SMS:a unique PIN is automatically generated and sent to the signer’s phone. The signer enters it in a login page and obtains access to the documents requiring the signature.
- Security question (static KBA): security questions are presented to the signer for authentication before he/she can view the electronic document(s). These questions are known as shared secrets because the sender needs to know something about the signer to create these questions. The questions and answers are known to both parties and pre-selected in advance. Common questions include the last four digits of the DNI or application ID number. The customer must correctly answer one or more questions before being given access to the electronic signature transaction.
- Dynamic KBA:OneSpan Sign can integrate with third-party identity verification services such as Equifax. The signer is presented with questions generated on the fly to authenticate his or her identity before signing the documents. These questions are generated in real time, making it difficult for anyone other than the actual user to answer correctly.
- Digital Certificates:OneSpan Sign leverages digital certificates issued by third-party trusted service providers and certificate authorities. When a personal digital certificate is used to electronically sign a document, the status of the certificate is verified and signers must pass the authentication requirements by combining the certificate with a PIN or password. When a digital certificate issued by a qualified trust service provider is used, a qualified electronic signature is created in accordance with the requirements of the European Union’s eIDAS regulation.
- Smart cards and earnedcredentials : Government employees and vendors require a smart card or earned mobile credentials when signing electronically. Digital certificates are stored on smart cards, such as common access cards and personal identity verification cards. This is a form of multi-factor authentication because it consists of something the user knows (the user’s smart card PIN), something the user has (the smart card) and sometimes even a biometric identifier (something the user is).
- Digipass®: multi-factor authentication provides a layered element of security by requiring two or more methods of verification before a signer can access and complete the transaction. OneSpan Sign integrates with OneSpan’s multi-factor authentication solutions such as
Digipass
to facilitate strong authentication with one-time passwords (OTP) and/or visual cryptograms during the initial user authentication step and/or at the time of signing. - Biometric data: Biometric data is generally used for high-risk, high-value transactions with existing customers. OneSpan Sign can be combined with OneSpan
Mobile Security Suite
to take advantage of fingerprint and facial recognition authentication methods to authenticate yourself before accessing documents that require your signature.
OneSpan Sign is an electronic signature solution that provides the flexibility to secure your authentication requirements for a variety of signing scenarios. Read our whitepaper on
User Identification and Authentication
for best practices on how to select the right authentication methods for your e-signature use case.
User authentication for electronic signatures
Learn how to select the correct authentication methods to prove who signed.
Content extracted from
OneSpan
.
