Privacy Policy
In accordance with the provisions of both Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data (RGPD), and the Organic Law 3/2018 of 5 December on the Protection of Personal Data and Guarantee of Digital Rights (LOPD-GDD) and other data protection regulations in force, the users of the website, who have voluntarily expressed their consent in a free, clear and unequivocal manner for the processing of personal data by accepting the “Data Protection Policy” box, are informed that their data will be processed, depending on the company with which they have contacted, either the company MAILTECK, S.A. or the company CUSTOMER COMMUNICATIONS TECKNALIA, S.L., which will be jointly referred to as MAILCOMMS GROUP within this Privacy Policy.
Identity: MailtecK, S.A.
NIF: A-31501901
Address: Avenida de la Recomba nº 12-14 – 28914 Leganés (Madrid)
Telephone: 91 304 49 41
E-mail: info@mailteck.com
Contact with the DPO: dpo@mailteck.com
Identity: Customer Communications Tecknalia, S.L.
NIF: B-86414000
Address: Avenida de la Recomba nº 12-14 – 28914 Leganés (Madrid)
Telephone: 91 689 56 65
E-mail: info@customercomms.com
Contact with the DPO: dpo@customercomms.com
In MAILCOMMS GROUP we process the data collected for:
- Web user data:
They will be treated only for statistical purposes and navigation analysis, to optimize and improve the user experience, all in accordance with the provisions of our Cookies Policy. In any case, these are non-invasive analyses that allow the improvement of services and the technology applied to them. - Data collected through the contact form:
The data will be processed in order to manage, process and respond to the request made through the contact forms made available on the website. - Subscription data to our Newsletter:
The data of subscribers to the Newsletter will be processed for the sole purpose of sending information about the activity of MAILCOMMS GROUP, as well as to inform them of news, promotions, events organized or discounts applicable to our products or services.
MAILCOMMS GROUP will only process the data provided for the purposes described above and will not be further processed in a manner incompatible with those purposes.
The personal data provided will be kept for the legal periods applicable in each case, taking into account the type of data, as well as the purpose of processing, as long as the user has not exercised his right of deletion.
No automated decisions will be made on the basis of such a profile.
- Web user data:
Legitimate interest, consisting of the continuous improvement of the business model offered on the website, as well as the correction of any deficiencies that may be detected in the delivery of the service. - Data collected through the contact form:
Consent of the person concerned by providing their data directly through the contact forms provided. - Subscription data to our Newsletter:
Consent of the person concerned by ticking the box provided for this purpose.
- Collaborating and participated companies for commercial purposes.
- By legal requirement when required by law.
- General confirmation: Any person has the right to obtain confirmation as to whether MAILCOMMS GROUP is processing personal data concerning them.
- ARCO Rights: Interested parties have the right to access their personal data, as well as to request the rectification of inaccurate data or, where appropriate, request its deletion when, among other reasons, the data is no longer necessary for the purposes for which it was collected.
- Limitation of processing: In certain circumstances, the interested parties may request the limitation of the processing of their data, in which case we will only keep them for the exercise or defense of claims.
- Opposition to processing: In certain circumstances and for reasons related to their particular situation, data subjects may object to the processing of their data.
Therefore, MAILCOMMS GROUP will stop processing the data, except for compelling legitimate reasons, or the exercise or defense of possible claims. - Data portability: In certain circumstances and for reasons related to their particular situation, data subjects may request to receive the personal data provided in the contact form, in a structured, commonly used and machine-readable format, as well as to transmit such data to another data controller without hindrance.
- Claim before a public body: If you consider that your right to personal data protection has been violated, you may file a claim before the Spanish Data Protection Agency (www.aepd.es).
- Channel to exercise the rights: Interested parties may exercise the rights recognized in the regulations against, and against, each of the responsible parties, before the addresses enabled as DPO in the “Responsible” section.
- The personal data have been obtained by the interested party by directly providing their data through the contact forms provided.
- The categories of data to be processed are identification data (name, surname, corporate e-mail, corporate telephone, position, company where you provide your services).
- MAILCOMMS GROUP does not process specially protected data.
Version: 9 | DATE: October 17, 2025
ANNEX I: INFORMATION SECURITY, CONTINUITY AND PRIVACY MANAGEMENT SYSTEM POLICY
This Information Security, Continuity and Privacy Policy shows the commitment of the Management by providing the organization with resources, responsibilities and procedures to ensure compliance with current regulations, as well as the integrity, confidentiality and availability of information and systems, which is crucial for the security, privacy and continuity of our organization, as well as that of our customers.
MailComms Group, aware that the security, continuity and privacy of information relating to our customers is a valuable resource, has established an Information Security, Continuity and Privacy Management System in accordance with the requirements of the ISO/IEC 27001, ISO/IEC 27701 and ISO 22301 standards to guarantee the continuity of information systems, minimize the risk of damage and ensure compliance with the objectives set.
Additionally, for qualified electronic trust services, based on the nature of the services provided, the provisions established in the European eIDAS Regulation governing Trusted Services have been followed, and specifically the ETSI 319 401, which is the general technical standard for all Trust Electronic Service Providers, ETSI 319 521 for Certified Electronic Delivery Service Providers and ETSI TS 119 511, for qualified electronic signature and seal preservation service providers, which contain specific precepts for the provision of each type of service. In this sense, the Policy that will govern these services will be the Trusted Service Practice Statement for each type of service (hereinafter “TPS”).
Furthermore, in compliance with European cybersecurity regulations, the entities that are part of the Group, in their capacity as Qualified Trust Service Providers, undertake to comply with Directive (EU) 2022/2555 on measures to ensure a common high level of cybersecurity throughout the Union, as essential entities of the European digital infrastructure.
The objective of the Security, Continuity and Privacy Policy is to establish the necessary action framework to protect information resources against threats, internal or external, deliberate or accidental, in order to ensure compliance with the confidentiality, integrity and availability of information.
The effectiveness and implementation of the Information Security, Continuity and Privacy Management System is the direct responsibility of the Information Security and Privacy Committee, which is responsible for the approval, dissemination and compliance with this Security, Continuity and Privacy Policy. In its name and on its behalf, an Information Security and Privacy Management System Manager has been appointed, who has sufficient authority to play an active role in the Information Security and Privacy Management System, supervising its implementation, development and maintenance.
In addition, and in order to comply with current data protection regulations, a Data Protection Officer (DPO) has been appointed to guarantee the security and privacy of personal data, especially taking into account the company’s activity.
The Information Security and Privacy Committee shall develop and approve the risk analysis methodology used in the Information Security, Continuity and Privacy Management System.
Any person whose activity may, directly or indirectly, be affected by the requirements of the Information Security, Continuity and Privacy Management System is obliged to strictly comply with the Security, Continuity and Privacy Policy and, additionally, for Qualified Trusted Electronic Services, must comply with the CPD of each service.
MailComms Group will implement all necessary measures to comply with the applicable regulations on security, continuity and privacy in general and computer security, relating to IT policy, the security of buildings and facilities and the behavior of employees and third parties associated with MailComms Group in the use of computer systems and the processing of personal data. The measures necessary to guarantee the security and privacy of information through the application of standards, procedures and controls shall ensure the confidentiality, integrity and availability of the information, essential to:
- Comply with current legislation, regulations and standards on continuity, privacy and information systems and with all contractual requirements regarding data protection and trusted electronic services, as well as those it deems appropriate to carry out with the aim of achieving continuous improvement of the organization and the security, continuity and privacy management system.
- To ensure the confidentiality of the data managed by MailComms Group.
- Ensure the availability of information systems, both in the services offered to customers and in internal management.
- Ensure the capacity to respond to emergency situations, restoring the operation of critical services in the shortest possible time.
- Avoid undue alterations in the information.
- Promote awareness and training in information security, continuity, privacy and trustworthy e-services.
- Promote and participate in achieving continuous improvement of the security management system, continuity and privacy of information and trustworthy electronic services.
- Establish technical and methodological requirements for cybersecurity risk management measures, identifying risks and correcting detected vulnerabilities, cyber threats and cybersecurity incidents, in order to prevent the materialization of incidents that compromise the business continuity of MailComms Group.
- Update the results of the risk assessment and risk treatment plan at planned intervals and at least once a year, and when there are significant changes in operations or significant risks or incidents.
The Information Security and Privacy Policy and CPD should be reviewed at planned intervals, at least annually and whenever significant changes occur in the organization, to ensure that their suitability, adequacy and effectiveness are maintained.
Madrid, October 17, 2025
Francisco Javier Echebarría Gangoiti
Avenida de la Recomba, 14 – 28914 Leganés
Version: 4 | DATE: December 4, 2024
NETWORK AND INFORMATION SYSTEMS SECURITY POLICY
The management of MailComms Group (formed by MAILTECK S.A. and CUSTOMER COMMUNICATIONS TECKNALIA S.L.), hereinafter “MailComms Group” or, specifically, “MailTecK” and/or “CCOMMS”, aware of the need to promote, maintain and improve the customer focus in all its activities, has implemented an Integrated Management System (IMS) in accordance with several internationally recognized standards. The ultimate goal of the SGI is to ensure that we understand and share our customers’ needs and goals, striving to provide services that meet their expectations and working towards continuous improvement. MailComms Group expressly states its commitment to enhance Information Security and Cybersecurity, specifically, to ensure, among others, the security of networks and information systems that support the various business processes in such a way as to strengthen its digital operational resilience, as well as the continuity and availability of the service provided, aligning its practices with the applicable regulations in force.
In this regard, MailComms Group is committed to developing maximum cybersecurity capabilities, thereby reducing threats to the network and information systems used by MailComms Group in compliance with European cybersecurity regulations.
At the same time, it is committed to satisfy the needs and expectations of the interested parties, to maintain high competitiveness in services and products for the “Automated processing of communications and multichannel transactions with customers, Issuance of documents in electronic and paper format, as well as Electronic Certification of security documents and Trust Services: Qualified Service of Certified Electronic Delivery, Electronic Contracting and Signature; Electronic and postal Notifications and Communications; Electronic Identification and Authentication and Digital Archiving”.
MAILCOMMS GROUP’S ROLE VIS-À-VIS DIRECTIVE (EU) 2022/2555
MAILTECK and CCOMMS, in their capacity as Qualified Trust Service Providers, are considered essential entities of the European digital infrastructure in accordance with Directive (EU) 2022/2555 on measures to ensure a high common level of cybersecurity throughout the Union, commonly referred to as the “NIS 2 Directive”, which entails their status as an obliged subject.
For this reason, this Policy is part of the security strategy pursued by MailComms Group, with the aim of ensuring that the use of networks and information systems complies with the rights of the parties concerned and safeguards the highest standards of cybersecurity, taking into account the Group’s activities and structure.
Therefore, MailComms Group will become responsible for compliance with the obligations required by these regulations.
MISSION and OBJECTIVES:
- Promote continuous improvement of services and customer support.
- Continue to position MailComms Group as a benchmark in the sector.
- Implement, maintain and test our business continuity mechanisms to ensure that vital information and services are available to our customers when needed.
- To provide customers with the most professional equipment and to have available immediately, and for as long as necessary, highly qualified technicians, experts in the required disciplines and accustomed to working as a team.
- Provide adequate resources necessary to implement this Policy, including personnel, financial resources, processes, tools and technologies.
- To have a service delivery based on our commitment to the continuous improvement of our systems, with security, cybersecurity and information continuity as a central pillar.
- Encourage and promote a culture of cybersecurity among all its professionals and subjects bound by this Policy, either internally, or among its customers and suppliers.
- Implement an information security culture through training and awareness-raising.
Our mission and objectives will be achieved through:
- A system of objectives, metrics and indicators for continuous improvement, follow-up, measurement of our internal processes, as well as customer satisfaction. Establishing and supervising compliance with contractual requirements to ensure an efficient and safe service.
- Integrate indicators linked to the level of implementation and maturity of security measures into the ISMS metrics system.
- Continuously training and raising the awareness of our team to have the highest degree of professionalism and specialization possible.
- Having our infrastructures in an adequate state and in accordance with the requirements of our customers.
- Organization and implementation of security processes.
- Personnel management.
- Authorization and access control.
- Default security.
- System integrity and updating.
- Protection of information stored and in transit.
- Prevention against other interconnected information systems.
- Implementing a secure product procurement management procedure.
- Complying with the requirements of current legislation, especially regarding Personal Data Protection: GDPR and LOPDGDD.
- Complying with the Policies and Procedures defined in our Security Documentation.
- Introducing continuous improvement processes that allow a permanent advance in our Information Security management.
- Managing and developing plans for risk management and treatment with a standards-based risk analysis and management methodology.
- Securely managing internal and external communications, as well as information stored and in transit.
- Ensuring interconnection with other information systems.
- Managing and monitoring activity with log management.
- Managing daily measures aimed at the protection and security of networks and information systems, designing robust security measures, aligned with the needs of the different stakeholders, as well as with the current applicable regulations on the subject, for which, MailComms Group approves the specific policies and/or procedures that develop the basic principles and requirements for the security of networks and information systems established in this Policy. The objective is to identify risks and correct detected vulnerabilities, cyber threats and cybersecurity incidents, in order to prevent the materialization of incidents that compromise the business continuity of MailComms Group.
- Defining policies and procedures for security incident management.
- Ensuring business and service continuity and availability.
- Ensuring that our Assets and Services comply with ENS HIGH Level measures for the dimensions of Confidentiality, Integrity, Availability, Authenticity and Traceability.
- Establishing, implementing and applying security procedures and/or policies in the supply chain that govern relations with direct suppliers and service providers and establishing the appropriate measures and controls in order to mitigate the risks detected derived from these third parties for the security of the Group’s networks and information systems.
In addition, these principles should be contemplated in the following safety areas:
- Physical: Comprising the security of premises, facilities, hardware systems, supports and any physical asset that processes or may process information, as well as physical access.
- Logical: Including aspects of protection of applications, networks, electronic communication, computer systems and logical access.
- Political-corporate: Made up of security aspects related to the organization itself, internal rules, regulations and legal norms.
The ultimate goal of information security is to ensure that an organization can meet its objectives using information systems. The following basic principles should be taken into account in security decisions:
- Organization and implementation of the security process.
- Risk analysis and management.
- Personnel management.
- Professionalism.
- Authorization and access control.
- Protection of facilities.
- Acquisition of security products and contracting of security services.
- Minimal privilege.
- System integrity and updating.
- Protection of information stored and in transit.
- Prevention against other interconnected information systems.
- Activity logging and detection of malicious code.
- Security incidents.
- Business continuity.
- Continuous improvement of the security process.
All cybersecurity documentation developed in execution of the requirements set out in this point is managed, structured and retained in accordance with the documented procedures that MailComms Group has developed taking into account the national and international technical standards and regulations that apply in each case. A minimum retention period of 5 years has been established for the regulatory framework and the evidence supporting compliance with the same in terms of cybersecurity. Within the framework of the Qualified Electronic Delivery Service, the Declarations of Practice (DPCs) and the final Declaration of the service will be kept for 15 years.
Security roles or functions within the ENS framework:
Responsible for the Information: shall determine the (security) requirements of the information processed, according to the parameters of Annex I of the ENS.
- You are ultimately responsible for the use made of the information and, therefore, for its protection. It is ultimately responsible for any error or negligence leading to an incident of confidentiality or integrity (in terms of data protection) and availability (in terms of information security).
System responsible: Determines the requirements of the services provided.
- It has the following functions:
- Develop, operate and maintain the information system throughout its life cycle, including its specifications, installation and verification of its correct functioning.
- Define the topology and management of the information system, establishing the criteria for its use and the services available in it.
- Ensure that security measures are properly integrated into the overall security framework.
Information Security Manager: Determines the decisions to satisfy the requirements of information security and services.
- The two essential functions of the Security Manager are:
- Maintain the security of the information handled and the services provided by the information systems in its area of responsibility, in accordance with the provisions of the organization’s Information Security Policy.
- Promote information security training and awareness within their area of responsibility.
Service Manager: Determines the (security) requirements of the services provided, according to the parameters of Annex I of the ENS.
- It has the power to establish the security requirements of the service. The determination of the levels in each security dimension is carried out within the framework established in Annex I of the National Security Scheme, the assessment criteria being supported by the Security Policy.
The MailComms Group ‘s Information Security and Privacy Committee (CSPI) , with the purpose of regulating and proceeding with the information security and privacy measures and policies, as well as the regulations aimed at adapting the information systems to the current personal data protection regulations, has, among other functions:
- Appoint the person in charge of the SGSPI and approve his/her functions.
- Approve the start of the implementation of the SGSPI.
- Review and approval of the Security and Privacy Policy.
- Approval of the Information Security and Privacy System Documentation, as well as new editions or modifications.
- Monitoring of the implementation and operation of the Information Security and Privacy System.
- Analysis of customer complaints.
- Periodically evaluate the degree of exposure to risks affecting MailComms Group’s information systems and personal data processing.
They make up the CSPI:
- General Manager.
- Technology Director.
- IT Operations Manager.
- Director of Printing Operations.
- Chief Financial, HR and Legal Officer.
- Commercial Director MailComms.
- Technical Director.
- Marketing Director.
- International Market Manager.
- Responsible for the SGSPI.
Considering these guidelines, this management reiterates its firm commitment to join efforts to achieve these objectives, so that this policy is understood, implemented and kept up to date at all levels of the organization.
Structuring of system safety documentation
The system documentation follows the following structure:
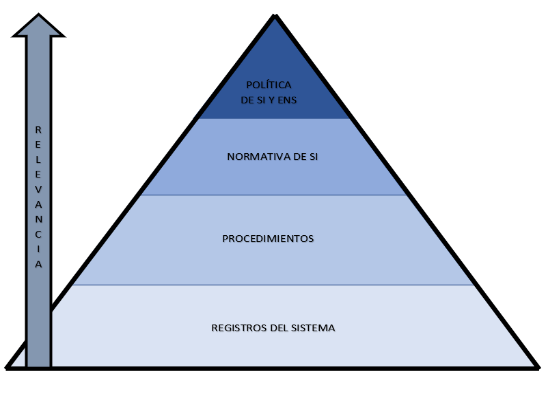
The classification of system information is classified into the following categories, as established in procedures PE-SGSPI 01-ERDS_Documentation Development and Control:
- Public Use
- Internal Use
- Confidential
Applicable legislation on the processing of personal data
With regard to the processing of personal data, the Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data and repealing Directive 95/46/EC and the corresponding national legislation shall mainly be taken into account.
The applicable legal and regulatory framework is included in document RE01-PE_SGSPI18 Applicable Standards and Legislation.
Follow-up, approval, publication and review
The CSPI must approve the entity’s Security, Cybersecurity, Continuity and Privacy Policies, publish and/or distribute them to all its employees, as well as to third parties that may be involved in the implementation of the information systems.
The person in charge of the SGSPI, and the person in charge of the corresponding Service, with regard to the specific policies of each service, shall be responsible for making them public or, where appropriate, communicating them and always maintaining them in MailComms Group’s systems.
The Policies for Information Security, Cybersecurity, Continuity and Privacy and the specific policies for each service must be reviewed at planned intervals, at least annually and whenever significant changes occur in the organization, in order to ensure that their suitability, adequacy and effectiveness are maintained.
The list of Policies applicable within the framework of the ENS and SGSPI-ERDS can be found in the document “RE01-PE SGSPI-ERDS 01 List of documents and records of the SGSPI-ERDS”.
On the other hand, the list of policies applicable within the framework of ERDS:
- MailTecK’s Certified Electronic Delivery Trusted Service Practices Statement.
- Customer Comms Certified Electronic Delivery Trusted Service Practices Statement.
Annex I Policy SGSPI-ERDS.
[1] Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 on measures for a common high level of cybersecurity across the Union, amending Regulation (EU) No 910/2014 and Directive (EU) 2018/1972 and repealing Directive 2016/1148.
LEGAL FRAMEWORK: Royal Decree 311/2022, of May 3, amending Royal Decree 3/2010, of January 8, which regulates the National Security Scheme in the field of Electronic Administration.